2.1: Security Fundamentals
The Goals of Information Security
Information security professionals have broad and important responsibilities for safeguarding the information and systems that are often an organization’s most valuable assets. When we think of the goals of information security, we often use a model known as the CIA triad, shown here.
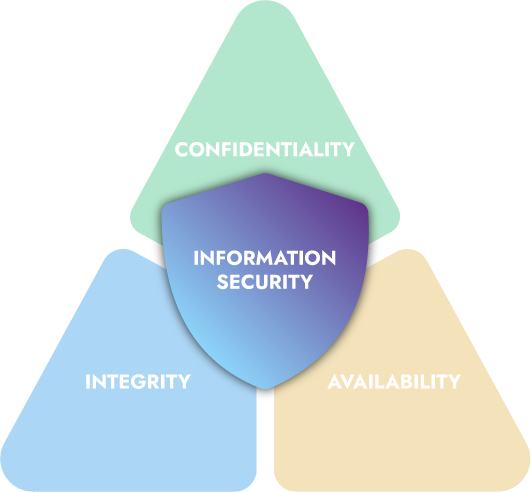
Confidentiality
Ensures that only authorized individuals have access to information and resources.
Integrity
Maintaining consistency, accuracy and trustworthiness of data over its lifecycle.
Availability
Information requested is readily available to authorized entity.
This model highlights the three most important functions that information security performs in an enterprise, confidentiality, integrity and availability.
Confidentiality
This is what most people think of when they think about cybersecurity, keeping secrets away from prying eyes. And the confidentiality is in fact how security professionals spend the majority of their time. Malicious individuals seeking to undermine confidentiality are said to engage in disclosure, making sensitive information available to individuals or the general public without the owner’s consent.
Integrity
This means that there aren’t any unauthorized changes made to that information. These unauthorized changes may come in the form of an attacker seeking to intentionally alter information, or a service disruption that accidentally affects data stored in a system. In either case, it’s the information security professional’s responsibility to prevent these lapses in integrity.
Availability
Ensuring that authorized individuals are able to gain access to information when they need it. If users can’t access important business records or systems, that lack of availability may have a profound impact on the business. Malicious individuals seeking to undermine availability engage in attacks known as denial of service attacks. These attacks try to either overwhelm a system or cause it to crash, therefore denying legitimate users the access that they need.